-
[따배쿠] Ingress - 웹페이지 구현kubernetes 2024. 12. 9. 11:08
Ingress를 이용한 웹 서비스 운영
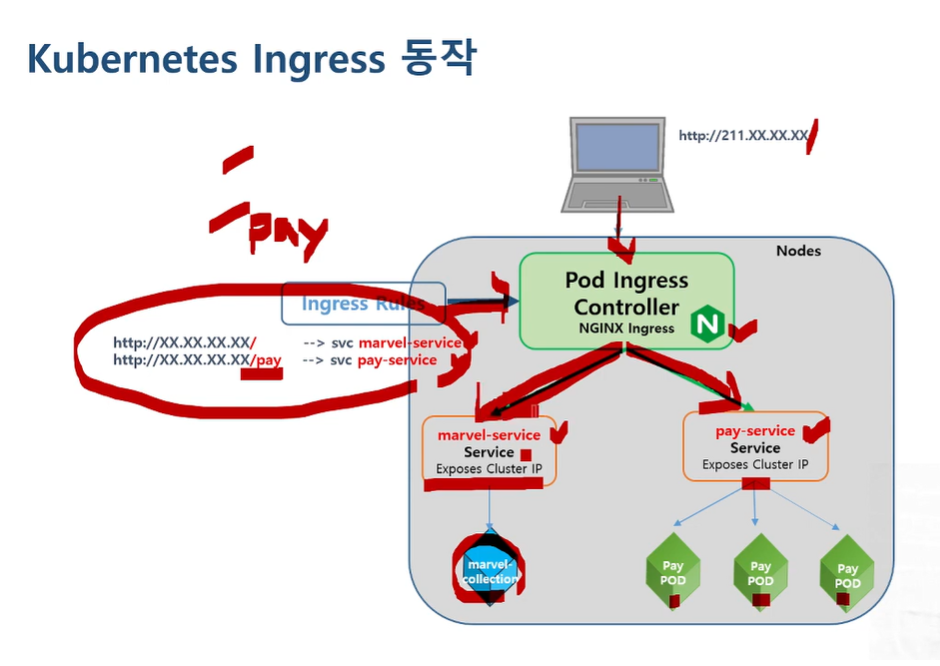
#1. Service 및 Pod 생성
marvel-service > marvel-collection pod
pay-service > pay pod, pay pod, pay pod
#2. Ingress Rules 생성
http://xx.xx.xx.xx/ > marvel-service
http://xx.xx.xx.xx/pay > pay-service
#3. Client 접속
http://xx.xx.xx.xx/ > marvel-service로 연결 되는지 확인
http://xx.xx.xx.xx/pay > pay-service로 연결 되는지 확인
즉, Client가 http://211.xxx.xxx.xx/로 접속하면, Pod Ingress Controller가 Ingress Rules을 참고하여 연결시켜준다.
- http://211.xxx.xxx.xx/ 접속 > marvel-service로 연결
- http://211.xxx.xxx.xx/pay 접속 > pay-service로 연결
실습
[Ingress-Controller 설치]
# Ingress-controller 설치 파일 작성
root@master:~/Getting-Start-Kubernetes/8# vi deploy.yaml apiVersion: v1 kind: Namespace metadata: name: ingress-nginx labels: app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx --- # Source: ingress-nginx/templates/controller-serviceaccount.yaml apiVersion: v1 kind: ServiceAccount metadata: labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: controller name: ingress-nginx namespace: ingress-nginx automountServiceAccountToken: true --- # Source: ingress-nginx/templates/controller-configmap.yaml apiVersion: v1 kind: ConfigMap metadata: labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: controller name: ingress-nginx-controller namespace: ingress-nginx data: --- # Source: ingress-nginx/templates/clusterrole.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm name: ingress-nginx rules: - apiGroups: - '' resources: - configmaps - endpoints - nodes - pods - secrets verbs: - list - watch - apiGroups: - '' resources: - nodes verbs: - get - apiGroups: - '' resources: - services verbs: - get - list - watch - apiGroups: - extensions - networking.k8s.io # k8s 1.14+ resources: - ingresses verbs: - get - list - watch - apiGroups: - '' resources: - events verbs: - create - patch - apiGroups: - extensions - networking.k8s.io # k8s 1.14+ resources: - ingresses/status verbs: - update - apiGroups: - networking.k8s.io # k8s 1.14+ resources: - ingressclasses verbs: - get - list - watch --- # Source: ingress-nginx/templates/clusterrolebinding.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm name: ingress-nginx roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: ingress-nginx subjects: - kind: ServiceAccount name: ingress-nginx namespace: ingress-nginx --- # Source: ingress-nginx/templates/controller-role.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: Role metadata: labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: controller name: ingress-nginx namespace: ingress-nginx rules: - apiGroups: - '' resources: - namespaces verbs: - get - apiGroups: - '' resources: - configmaps - pods - secrets - endpoints verbs: - get - list - watch - apiGroups: - '' resources: - services verbs: - get - list - watch - apiGroups: - extensions - networking.k8s.io # k8s 1.14+ resources: - ingresses verbs: - get - list - watch - apiGroups: - extensions - networking.k8s.io # k8s 1.14+ resources: - ingresses/status verbs: - update - apiGroups: - networking.k8s.io # k8s 1.14+ resources: - ingressclasses verbs: - get - list - watch - apiGroups: - '' resources: - configmaps resourceNames: - ingress-controller-leader-nginx verbs: - get - update - apiGroups: - '' resources: - configmaps verbs: - create - apiGroups: - '' resources: - events verbs: - create - patch --- # Source: ingress-nginx/templates/controller-rolebinding.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: controller name: ingress-nginx namespace: ingress-nginx roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: ingress-nginx subjects: - kind: ServiceAccount name: ingress-nginx namespace: ingress-nginx --- # Source: ingress-nginx/templates/controller-service-webhook.yaml apiVersion: v1 kind: Service metadata: labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: controller name: ingress-nginx-controller-admission namespace: ingress-nginx spec: type: ClusterIP ports: - name: https-webhook port: 443 targetPort: webhook selector: app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/component: controller --- # Source: ingress-nginx/templates/controller-service.yaml apiVersion: v1 kind: Service metadata: annotations: labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: controller name: ingress-nginx-controller namespace: ingress-nginx spec: type: NodePort ports: - name: http port: 80 protocol: TCP targetPort: http nodePort: 30100 - name: https port: 443 protocol: TCP targetPort: https nodePort: 30200 selector: app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/component: controller --- # Source: ingress-nginx/templates/controller-deployment.yaml apiVersion: apps/v1 kind: Deployment metadata: labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: controller name: ingress-nginx-controller namespace: ingress-nginx spec: selector: matchLabels: app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/component: controller revisionHistoryLimit: 10 minReadySeconds: 0 template: metadata: labels: app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/component: controller spec: dnsPolicy: ClusterFirst containers: - name: controller image: k8s.gcr.io/ingress-nginx/controller:v0.45.0@sha256:c4390c53f348c3bd4e60a5dd6a11c35799ae78c49388090140b9d72ccede1755 imagePullPolicy: IfNotPresent lifecycle: preStop: exec: command: - /wait-shutdown args: - /nginx-ingress-controller - --election-id=ingress-controller-leader - --ingress-class=nginx - --configmap=$(POD_NAMESPACE)/ingress-nginx-controller - --validating-webhook=:8443 - --validating-webhook-certificate=/usr/local/certificates/cert - --validating-webhook-key=/usr/local/certificates/key securityContext: capabilities: drop: - ALL add: - NET_BIND_SERVICE runAsUser: 101 allowPrivilegeEscalation: true env: - name: POD_NAME valueFrom: fieldRef: fieldPath: metadata.name - name: POD_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace - name: LD_PRELOAD value: /usr/local/lib/libmimalloc.so livenessProbe: httpGet: path: /healthz port: 10254 scheme: HTTP initialDelaySeconds: 10 periodSeconds: 10 timeoutSeconds: 1 successThreshold: 1 failureThreshold: 5 readinessProbe: httpGet: path: /healthz port: 10254 scheme: HTTP initialDelaySeconds: 10 periodSeconds: 10 timeoutSeconds: 1 successThreshold: 1 failureThreshold: 3 ports: - name: http containerPort: 80 protocol: TCP - name: https containerPort: 443 protocol: TCP - name: webhook containerPort: 8443 protocol: TCP volumeMounts: - name: webhook-cert mountPath: /usr/local/certificates/ readOnly: true resources: requests: cpu: 100m memory: 90Mi nodeSelector: kubernetes.io/os: linux serviceAccountName: ingress-nginx terminationGracePeriodSeconds: 300 volumes: - name: webhook-cert secret: secretName: ingress-nginx-admission --- # Source: ingress-nginx/templates/admission-webhooks/validating-webhook.yaml # before changing this value, check the required kubernetes version # https://kubernetes.io/docs/reference/access-authn-authz/extensible-admission-controllers/#prerequisites apiVersion: admissionregistration.k8s.io/v1 kind: ValidatingWebhookConfiguration metadata: labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: admission-webhook name: ingress-nginx-admission webhooks: - name: validate.nginx.ingress.kubernetes.io matchPolicy: Equivalent rules: - apiGroups: - networking.k8s.io apiVersions: - v1beta1 operations: - CREATE - UPDATE resources: - ingresses failurePolicy: Fail sideEffects: None admissionReviewVersions: - v1 - v1beta1 clientConfig: service: namespace: ingress-nginx name: ingress-nginx-controller-admission path: /networking/v1beta1/ingresses --- # Source: ingress-nginx/templates/admission-webhooks/job-patch/serviceaccount.yaml apiVersion: v1 kind: ServiceAccount metadata: name: ingress-nginx-admission annotations: helm.sh/hook: pre-install,pre-upgrade,post-install,post-upgrade helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: admission-webhook namespace: ingress-nginx --- # Source: ingress-nginx/templates/admission-webhooks/job-patch/clusterrole.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: ingress-nginx-admission annotations: helm.sh/hook: pre-install,pre-upgrade,post-install,post-upgrade helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: admission-webhook rules: - apiGroups: - admissionregistration.k8s.io resources: - validatingwebhookconfigurations verbs: - get - update --- # Source: ingress-nginx/templates/admission-webhooks/job-patch/clusterrolebinding.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: ingress-nginx-admission annotations: helm.sh/hook: pre-install,pre-upgrade,post-install,post-upgrade helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: admission-webhook roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: ingress-nginx-admission subjects: - kind: ServiceAccount name: ingress-nginx-admission namespace: ingress-nginx --- # Source: ingress-nginx/templates/admission-webhooks/job-patch/role.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: Role metadata: name: ingress-nginx-admission annotations: helm.sh/hook: pre-install,pre-upgrade,post-install,post-upgrade helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: admission-webhook namespace: ingress-nginx rules: - apiGroups: - '' resources: - secrets verbs: - get - create --- # Source: ingress-nginx/templates/admission-webhooks/job-patch/rolebinding.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: ingress-nginx-admission annotations: helm.sh/hook: pre-install,pre-upgrade,post-install,post-upgrade helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: admission-webhook namespace: ingress-nginx roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: ingress-nginx-admission subjects: - kind: ServiceAccount name: ingress-nginx-admission namespace: ingress-nginx --- # Source: ingress-nginx/templates/admission-webhooks/job-patch/job-createSecret.yaml apiVersion: batch/v1 kind: Job metadata: name: ingress-nginx-admission-create annotations: helm.sh/hook: pre-install,pre-upgrade helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: admission-webhook namespace: ingress-nginx spec: template: metadata: name: ingress-nginx-admission-create labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: admission-webhook spec: containers: - name: create image: docker.io/jettech/kube-webhook-certgen:v1.5.1 imagePullPolicy: IfNotPresent args: - create - --host=ingress-nginx-controller-admission,ingress-nginx-controller-admission.$(POD_NAMESPACE).svc - --namespace=$(POD_NAMESPACE) - --secret-name=ingress-nginx-admission env: - name: POD_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace restartPolicy: OnFailure serviceAccountName: ingress-nginx-admission securityContext: runAsNonRoot: true runAsUser: 2000 --- # Source: ingress-nginx/templates/admission-webhooks/job-patch/job-patchWebhook.yaml apiVersion: batch/v1 kind: Job metadata: name: ingress-nginx-admission-patch annotations: helm.sh/hook: post-install,post-upgrade helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: admission-webhook namespace: ingress-nginx spec: template: metadata: name: ingress-nginx-admission-patch labels: helm.sh/chart: ingress-nginx-3.27.0 app.kubernetes.io/name: ingress-nginx app.kubernetes.io/instance: ingress-nginx app.kubernetes.io/version: 0.45.0 app.kubernetes.io/managed-by: Helm app.kubernetes.io/component: admission-webhook spec: containers: - name: patch image: docker.io/jettech/kube-webhook-certgen:v1.5.1 imagePullPolicy: IfNotPresent args: - patch - --webhook-name=ingress-nginx-admission - --namespace=$(POD_NAMESPACE) - --patch-mutating=false - --secret-name=ingress-nginx-admission - --patch-failure-policy=Fail env: - name: POD_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace restartPolicy: OnFailure serviceAccountName: ingress-nginx-admission securityContext: runAsNonRoot: true runAsUser: 2000# 생성 및 확인
root@master:~/Getting-Start-Kubernetes/8# kubectl create -f deploy.yaml namespace/ingress-nginx created serviceaccount/ingress-nginx created configmap/ingress-nginx-controller created clusterrole.rbac.authorization.k8s.io/ingress-nginx created clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx created role.rbac.authorization.k8s.io/ingress-nginx created rolebinding.rbac.authorization.k8s.io/ingress-nginx created service/ingress-nginx-controller-admission created service/ingress-nginx-controller created deployment.apps/ingress-nginx-controller created validatingwebhookconfiguration.admissionregistration.k8s.io/ingress-nginx-admission created serviceaccount/ingress-nginx-admission created clusterrole.rbac.authorization.k8s.io/ingress-nginx-admission created clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created role.rbac.authorization.k8s.io/ingress-nginx-admission created rolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created job.batch/ingress-nginx-admission-create created job.batch/ingress-nginx-admission-patch createdroot@master:~/Getting-Start-Kubernetes/8# kubectl get namespace NAME STATUS AGE default Active 35d ingress-nginx Active 58s kube-node-lease Active 35d kube-public Active 35d kube-system Active 35dingress-nginx라는 namespace가 생성된 것을 확인
root@master:~/Getting-Start-Kubernetes/8# kubectl get all -n ingress-nginx NAME READY STATUS RESTARTS AGE pod/ingress-nginx-admission-create-x8s4x 0/1 Completed 0 2m17s pod/ingress-nginx-admission-patch-htjbh 0/1 CrashLoopBackOff 4 (39s ago) 2m17s pod/ingress-nginx-controller-79fc5cfc7d-gqwmf 0/1 Running 1 (59s ago) 2m18s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/ingress-nginx-controller NodePort 10.99.3.156 <none> 80:30100/TCP,443:30200/TCP 2m18s service/ingress-nginx-controller-admission ClusterIP 10.108.62.104 <none> 443/TCP 2m18s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/ingress-nginx-controller 0/1 1 0 2m18s NAME DESIRED CURRENT READY AGE replicaset.apps/ingress-nginx-controller-79fc5cfc7d 1 1 0 2m18s NAME STATUS COMPLETIONS DURATION AGE job.batch/ingress-nginx-admission-create Complete 1/1 10s 2m17s job.batch/ingress-nginx-admission-patch Running 0/1 2m17s 2m17s해당 namespace를 가진 모든 리소스 조회
[namespace 치환]

작업을 편하게 하기 위해서, 기본 namespace를 default에서 Ingress-nginx로 바꿔보자
# 현재 namespace 확인
root@master:~/Getting-Start-Kubernetes/8# kubectl get namespaces NAME STATUS AGE default Active 35d kube-node-lease Active 35d kube-public Active 35d kube-system Active 35d orange Active 29d product Active 5d22h# 기본 namespace 변경
root@master:~/Getting-Start-Kubernetes/8# kubectl config set-context --current --namespace=ingress-nginx Context "kubernetes-admin@kubernetes" modified.
[웹 서비스 생성]
[웹 서비스 1 : marvel-home.yaml]
root@master:~/Getting-Start-Kubernetes/8/webserver-demo/ingress# vi marvel-home.yaml apiVersion: apps/v1 kind: Deployment metadata: name: marvel-home spec: replicas: 1 selector: matchLabels: name: marvel template: metadata: labels: name: marvel spec: containers: - image: smlinux/marvel-collection name: marvel-container ports: - containerPort: 80 --- apiVersion: v1 kind: Service metadata: name: marvel-service spec: ports: - port: 80 protocol: TCP targetPort: 80 selector: name: marvelsmlinux/marvel-collection이라는 이미지를 쓰는 marvel-home Pod를 1개 생성한다.
해당 Pod의 단일 진입점(Service)을 생성한다.
[웹 서비스 2: pay.yaml]
root@master:~/Getting-Start-Kubernetes/8/webserver-demo/ingress# vi pay.yaml apiVersion: v1 kind: ReplicationController metadata: name: pay-rc spec: replicas: 3 template: metadata: labels: app: pay spec: containers: - image: smlinux/pay name: pay ports: - containerPort: 8080 --- apiVersion: v1 kind: Service metadata: name: pay-service spec: ports: - port: 80 targetPort: 8080 selector: app: paysmlinux/pay 이라는 이미지를 쓰는 Pod를 ReplicationController를 통해 3개 생성한다.
해당 Pod의 단일 진입점(Service)을 생성한다.
# 생성
root@master:~/Getting-Start-Kubernetes/8/webserver-demo/ingress# kubectl create -f marvel-home.yaml -f pay.yaml deployment.apps/marvel-home created service/marvel-service created replicationcontroller/pay-rc created service/pay-service created# 확인
root@master:~/Getting-Start-Kubernetes/8/webserver-demo/ingress# kubectl get all NAME READY STATUS RESTARTS AGE pod/ingress-nginx-admission-create-dwvbk 0/1 Completed 0 24m pod/ingress-nginx-controller-79fc5cfc7d-wzhdn 0/1 Running 10 (6m7s ago) 24m pod/marvel-home-655d6f7cd8-79hp8 1/1 Running 0 92s pod/pay-rc-54mjt 1/1 Running 0 92s pod/pay-rc-h47hm 1/1 Running 0 92s pod/pay-rc-tpvmt 1/1 Running 0 92s NAME DESIRED CURRENT READY AGE replicationcontroller/pay-rc 3 3 3 92s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/ingress-nginx-controller NodePort 10.99.193.114 <none> 80:30100/TCP,443:30200/TCP 24m service/ingress-nginx-controller-admission ClusterIP 10.100.148.64 <none> 443/TCP 24m service/marvel-service ClusterIP 10.106.75.9 <none> 80/TCP 92s service/pay-service ClusterIP 10.110.111.103 <none> 80/TCP 92s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/ingress-nginx-controller 0/1 1 0 24m deployment.apps/marvel-home 1/1 1 1 92s NAME DESIRED CURRENT READY AGE replicaset.apps/ingress-nginx-controller-79fc5cfc7d 1 1 0 24m replicaset.apps/marvel-home-655d6f7cd8 1 1 1 92s NAME STATUS COMPLETIONS DURATION AGE job.batch/ingress-nginx-admission-create Complete 1/1 5s 24m job.batch/ingress-nginx-admission-patch Failed 0/1 24m 24m
[Ingress Rule 생성]
Pod Ingress Controller에서 작동할 Ingress Rule을 생성하자.
# ingress.yaml 파일 작성
root@master:~/Getting-Start-Kubernetes/8/webserver-demo/ingress# vi ingress.yaml apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: marvel-ingress spec: rules: - http: paths: - path: / pathType: Prefix backend: service: name: marvel-service port: number: 80 - path: /pay pathType: Prefix backend: service: name: pay-service port: number: 80/(루트)로 오는 건 marvel-service로 연결
/pay로 오는건 pay-service로 연결하는 Ingress Rule 생성
# 생성
root@master:~/Getting-Start-Kubernetes/8/webserver-demo/ingress# kubectl create -f ingress.yaml ingress.networking.k8s.io/marvel-ingress created# 확인
root@master:~/Getting-Start-Kubernetes/8/webserver-demo/ingress# kubectl describe ingress marvel-ingress Name: marvel-ingress Labels: <none> Namespace: ingress-nginx Address: Ingress Class: <none> Default backend: <default> Rules: Host Path Backends ---- ---- -------- * / marvel-service:80 (192.168.104.29:80) /pay pay-service:80 (192.168.104.28:8080,192.168.166.163:8080,192.168.166.172:8080) Annotations: <none> Events: <none>
참고 영상
https://www.youtube.com/watch?v=9TMIetXb6Pw
'kubernetes' 카테고리의 다른 글
[따배쿠] Node Label (2) 2024.12.10 [따배쿠] Label (1) 2024.12.10 [따배쿠] Ingress - 개념 및 설치 (0) 2024.12.09 [따배쿠] Headless Service, Kube-Proxy (0) 2024.12.08 [따배쿠] Service - ClusterIP, NodePort, LoadBalancer, ExternalName (1) 2024.12.07