[따배쿠] 인증과 권한 관리 - 권한관리편
권한 관리 (Role & RoleBinding)





실습
[Role 생성]
# command로 Role 생성
kubectl create role developer --verb=create --verb=get --verb=list --verb=update --verb=delete --resource=pods
role 이름 : develpoer
role 역할 : create, get, list, update, delete
대상 리소스 : pod
즉, pod에 대해 create, get, list, update, delete의 권한을 갖는 role이다.
# command로 만든 Role에 관해 yaml 파일로 확인
root@master:~# kubectl create role developer --verb=create --verb=get --verb=list --verb=update --verb=delete --resource=pods --dry-run -o yaml
W1229 06:37:41.385507 649542 helpers.go:703] --dry-run is deprecated and can be replaced with --dry-run=client.
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
creationTimestamp: null
name: developer
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- create
- get
- list
- update
- delete
[Role binding]
# command로 Role Binding
kubectl create rolebinding developer-binding-myuser --role=developer --user=myuser
# command로 만든 Role Binding에 관해 yaml 파일로 확인
root@master:~# kubectl create rolebinding developer-binding-myuser --role=developer --user=myuser
rolebinding.rbac.authorization.k8s.io/developer-binding-myuser created
root@master:~# kubectl create rolebinding developer-binding-myuser --role=developer --user=myuser --dry-run -o yaml
W1229 06:40:35.843526 650777 helpers.go:703] --dry-run is deprecated and can be replaced with --dry-run=client.
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: null
name: developer-binding-myuser
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: developer
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: myuser
즉, 지금까지 myuser를 쿠버네티스에 등록했고
해당 myuser에 developer이라는 Role을 Binding했다.
[해당 user을 kubeconfig에 추가]
# 새로운 자격증명 추가
root@master:~/Getting-Start-Kubernetes/13# kubectl config set-credentials myuser --client-key=myuser.key --client-certificate=myuser.crt --embed-certs=true
User "myuser" set.
# context 추가
root@master:~/Getting-Start-Kubernetes/13# kubectl config set-context myuser --cluster=kubernetes --user=myuser
Context "myuser" created.
myuser라는 context가 추가되었다.
# 작업 context switch
root@master:~/Getting-Start-Kubernetes/13# kubectl config use-context myuser
Switched to context "myuser".
# 현재 context 확인
root@master:~/Getting-Start-Kubernetes/13# kubectl config current-context
myuser
myuser의 작업 context로 switch 되었다.
# 테스트
root@master:~/Getting-Start-Kubernetes/13# kubectl get pods
No resources found in default namespace.
pod는 조회가 가능하다
root@master:~/Getting-Start-Kubernetes/13# kubectl get svc
Error from server (Forbidden): services is forbidden: User "myuser" cannot list resou rce "services" in API group "" in the namespace "default"
myuser은 pod에 대한 특정 권한만 갖고있으므로,
service에 대한 조회는 불가능하다. (권한이 없기 때문)
이렇게 user 별로 최소 권한을 제어할 수 있다.
root@master:~/Getting-Start-Kubernetes/13# kubectl get pods -n kube-system
Error from server (Forbidden): pods is forbidden: User "myuser" cannot list reso urce "pods" in API group "" in the namespace "kube-system"
같은 namespace(default)가 아닌 다른 namespace(kube-system)의 리소스는 확인 불가능하다.
권한 관리 (ClusterRole & ClusterRoleBinding)

일반 RoleBinding은 같은 namespace 안 리소스들에 대한 액세스 제어가 가능했다면, (자신이 속한 namespace)
ClusterRoleBidning은 같은 namespace 안 리소스뿐만 아니라 다른 namespace까지도 제어가 가능하다. (All namespace)
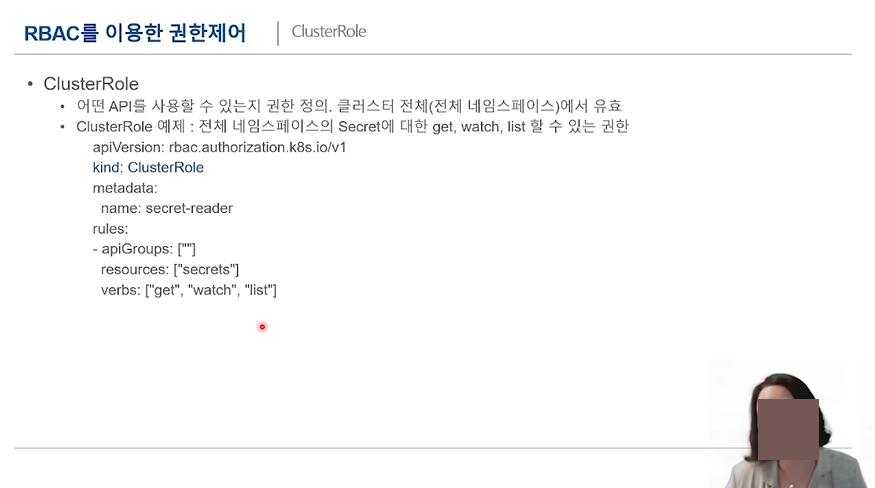
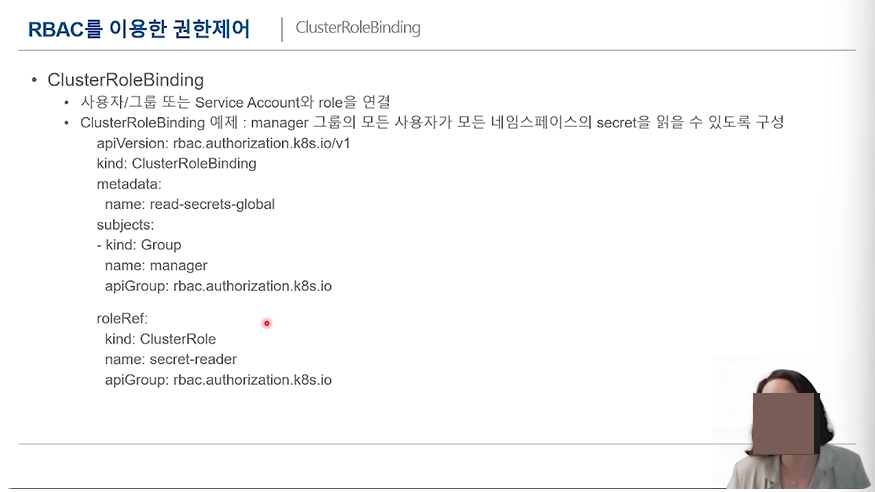
실습
기존의 Role과 RoleBinding을 삭제시켜보자
# 현재 context 확인
root@master:~/Getting-Start-Kubernetes/13# kubectl config current-context
myuser
# context 전환
root@master:~/Getting-Start-Kubernetes/13# kubectl config use-context kubernetes-admin@kubernetes
Switched to context "kubernetes-admin@kubernetes".root@master:~/Getting-Start-Kubernetes/13# kubectl config current-context kubernetes-admin@kubernetes
# role 확인 및 삭제
root@master:~/Getting-Start-Kubernetes/13# kubectl get role
NAME CREATED AT
developer 2024-12-29T08:05:49Zroot@master:~/Getting-Start-Kubernetes/13# kubectl delete role developer
role.rbac.authorization.k8s.io "developer" deleted
# roleBinding 확인 및 삭제
root@master:~/Getting-Start-Kubernetes/13# kubectl get rolebinding
NAME ROLE AGE
developer-binding-myuser Role/developer 22mroot@master:~/Getting-Start-Kubernetes/13# kubectl delete rolebinding developer-binding-myuser
rolebinding.rbac.authorization.k8s.io "developer-binding-myuser" deleted
ClusteRoleBinding 생성 뒤
다른 namespace의 리소스에도 접근 가능하도록 해보자
# ClusterRole 생성
root@master:~/Getting-Start-Kubernetes/13# kubectl create clusterrole developer --verb=create --verb=get --verb=list --verb=update --verb=delete --resource=pods clusterrole.rbac.authorization.k8s.io/developer created
# ClusterRoleBinding 생성
root@master:~/Getting-Start-Kubernetes/13# kubectl create clusterrolebinding developer-binding-myuser --clusterrole=developer --user=myuser
clusterrolebinding.rbac.authorization.k8s.io/developer-binding-myuser created
# context 전환
root@master:~/Getting-Start-Kubernetes/13# kubectl config use-context myuser
Switched to context "myuser".
myuser context로 전환한다.
# 테스트
root@master:~/Getting-Start-Kubernetes/13# kubectl get pods
No resources found in default namespace.
myuser가 위치한 default namespace의 리소스는 당연히 확인가능하다.
root@master:~/Getting-Start-Kubernetes/13# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
calico-kube-controllers-5b9b456c66-slbt7 1/1 Running 10 (27h ago) 24d
calico-node-22qcb 1/1 Running 17 (27h ago) 56d
calico-node-7lxq2 1/1 Running 10 (27h ago) 24d
calico-node-hqlgk 1/1 Running 17 (27h ago) 56d
coredns-55cb58b774-hn85c 1/1 Running 10 (27h ago) 24d
coredns-55cb58b774-wx9q6 1/1 Running 10 (27h ago) 24d
etcd-master 1/1 Running 17 (27h ago) 56d
kube-apiserver-master 1/1 Running 17 (27h ago) 56d
kube-controller-manager-master 1/1 Running 17 (27h ago) 56d
kube-proxy-4gkx6 1/1 Running 17 (27h ago) 56d
kube-proxy-6xskg 1/1 Running 10 (27h ago) 24d
kube-proxy-bbl9f 1/1 Running 17 (27h ago) 56d
kube-scheduler-master 1/1 Running 17 (27h ago) 56d
또한 다른 namespace 내 리소스까지 확인 가능하다.
root@master:~/Getting-Start-Kubernetes/13# kubectl get nodes
Error from server (Forbidden): nodes is forbidden: User "myuser" cannot list resource "nodes" in API group "" at the cluster scoperoot@master:~/Getting-Start-Kubernetes/13# kubectl get svc
Error from server (Forbidden): services is forbidden: User "myuser" cannot list resource "services" in API group "" in the namespace "default"
그러나 pod에 대해서만 접근 가능하도록 했으므로, pod를 제외한 다른 서비스에는 접근이 불가능하다.
삭제
# Context 변환
root@master:~/Getting-Start-Kubernetes/13# kubectl config use-context kubernetes-admin@kubernetes
Switched to context "kubernetes-admin@kubernetes".
# ClusterRole 및 ClusterRoleBinding 삭제
root@master:~/Getting-Start-Kubernetes/13# kubectl delete clusterrolebinding developer-binding-myuser
clusterrolebinding.rbac.authorization.k8s.io "developer-binding-myuser" deleted
root@master:~/Getting-Start-Kubernetes/13# kubectl delete clusterrole developer
clusterrole.rbac.authorization.k8s.io "developer" deleted
# User의 Context 삭제
root@master:~/Getting-Start-Kubernetes/13# kubectl config delete-context myuser
deleted context myuser from /root/.kube/config
# User 정보 삭제
root@master:~/Getting-Start-Kubernetes/13# kubectl config delete-user myuser
deleted user myuser from /root/.kube/config
# User 삭제
root@master:~/Getting-Start-Kubernetes/13# kubectl delete csr myuser
certificatesigningrequest.certificates.k8s.io "myuser" deleted
번외)
# 쿠버네티스에서 기본적으로 제공하는 cluster role
root@master:~/Getting-Start-Kubernetes/13# kubectl get clusterrole
NAME CREATED AT
admin 2024-11-03T05:00:43Z
calico-kube-controllers 2024-11-03T05:10:31Z
calico-node 2024-11-03T05:10:31Z
cluster-admin 2024-11-03T05:00:43Z
edit 2024-11-03T05:00:43Z
ingress-nginx 2024-12-09T04:50:36Z
ingress-nginx-admission 2024-12-09T04:50:37Z
kubeadm:get-nodes 2024-11-03T05:00:44Z
...
여기서 cluster-admin이라는 role을 자세하게 조회해보자
root@master:~/Getting-Start-Kubernetes/13# kubectl describe clusterrole cluster-admin
Name: cluster-admin
Labels: kubernetes.io/bootstrapping=rbac-defaults
Annotations: rbac.authorization.kubernetes.io/autoupdate: true
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
*.* [] [] [*]
[*] [] [*]
모든 리소스에 대해 모든 권한을 가지는 것을 확인 가능
root@master:~/Getting-Start-Kubernetes/13# kubectl create clusterrolebinding developer-binding-myuser --clusterrole=cluster-admin --user=myuser
clusterrole에 쓰면서 활용할 수 있다.
퀴즈

# user 및 csr 생성
root@master:~/Getting-Start-Kubernetes/13# openssl genrsa -out app-manager.key 2048
root@master:~/Getting-Start-Kubernetes/13# openssl req -new -key app-manager.key -out app-manager.csr -subj "/CN=app-manager"root@master:~/Getting-Start-Kubernetes/13# cat app-manager.csr | base64 | tr -d "\n"
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1d6Q0NBVU1DQVFBd0ZqRVVNQklHQTFVRUF3d0xZWEJ3TFcxaGJtRm5aWEl3Z2dFaU1BMEdDU3FHU0liMwpEUUVCQVFVQUE0SUJEd0F3Z2dFS0FvSUJBUUN4dU1CaDJDWVJsL0gxQnFRUHJNSW1nbmFCbzlEeElxYm1kN0g0CjJYWk9EU3BsL3lEa1pld1c1aHNLNVg3YkY1K2N2T2VhcEFMTHBTMU15QlIwZTZwRHBodGNUVDNMa2lQT2RDTnAKbkRsQjVGR3ZMUlIrYWlYY1JCMFhKZTNBRGtqSWFaZEFmeFB0VWQyMGJ5ekZaMjVCWU43VFpkSk85L0tjUzFXRgpOUWhqTDNLRmJLeVk0eUszZHg4OXk0ZE1wMEN1VjlNU2lOcy82TzdPMm5zNFpEaERMUDk5ZkNhaGhocnByK3hGCmVCUnlSeGZuczNIcWtzWnk0NStwbkV3Tk1aaU5PZmIrTkRiQlhSSU1qdUhodzF3VUlDQm82em9MQ0Njbm1YSHkKRzVCN29HTWdlelgwdDJPK3dZVmVucmxVRzI1NTByaTlvYkgvK2tzb3J3TjNzK0tMQWdNQkFBR2dBREFOQmdrcQpoa2lHOXcwQkFRc0ZBQU9DQVFFQVdUeU1BRmNLRTVZc1JMVXlvTVhLaFQxVi9EWjJpUCtuZDVVbTJIQnVaRHAxCm9LUWRVcDRmbzdqeGJGY0RSazJLTGRZNmtEOU5QaHh1STBTRk9DZjQyeFEvalh6NlVEQ3Q1cGtNdmpUdzBoVVQKTmJSbWtLVFQxSS9oOExxNTUrL1R5eDdiN3ppRzJwRzVRNFQ5VjNndHRJb2NvRFZGbTV6TDFUWFBXSFZ5QW5ucQpPTE9BV3hrL2pmTU1NN01zTnRqZ2Uxc1o3K3E3WXQxYTU4ZGhGbzVPalRmRHFVaERSSlFEZ2ZiVkVyQmRnWVZhCmg4SlNERGVwbHQ4dnZ6M2VQRU0xMEVnU1huaUJReS8zS2tEQjRoblNCSENGQk5CUFRXems0cEZkUDVMZUZ5cTcKZW9uMzdHdHYvM2FqU1Uwby9mYWxsRnQvOVliQ1RHaVAwRmZhNzFHY3VBPT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUgUkVRVUVTVC0tLS0tCg==
root@master:~/Getting-Start-Kubernetes/13# vi csr-app-manager.yaml
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
name: app-manager
spec:
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1d6Q0NBVU1DQVFBd0ZqRVVNQklHQTFVRUF3d0xZWEJ3TFcxaGJtRm5aWEl3Z2dFaU1BMEdDU3FHU0liMwpEUUVCQVFVQUE0SUJEd0F3Z2dFS0FvSUJBUUN4dU1CaDJDWVJsL0gxQnFRUHJNSW1nbmFCbzlEeElxYm1kN0g0CjJYWk9EU3BsL3lEa1pld1c1aHNLNVg3YkY1K2N2T2VhcEFMTHBTMU15QlIwZTZwRHBodGNUVDNMa2lQT2RDTnAKbkRsQjVGR3ZMUlIrYWlYY1JCMFhKZTNBRGtqSWFaZEFmeFB0VWQyMGJ5ekZaMjVCWU43VFpkSk85L0tjUzFXRgpOUWhqTDNLRmJLeVk0eUszZHg4OXk0ZE1wMEN1VjlNU2lOcy82TzdPMm5zNFpEaERMUDk5ZkNhaGhocnByK3hGCmVCUnlSeGZuczNIcWtzWnk0NStwbkV3Tk1aaU5PZmIrTkRiQlhSSU1qdUhodzF3VUlDQm82em9MQ0Njbm1YSHkKRzVCN29HTWdlelgwdDJPK3dZVmVucmxVRzI1NTByaTlvYkgvK2tzb3J3TjNzK0tMQWdNQkFBR2dBREFOQmdrcQpoa2lHOXcwQkFRc0ZBQU9DQVFFQVdUeU1BRmNLRTVZc1JMVXlvTVhLaFQxVi9EWjJpUCtuZDVVbTJIQnVaRHAxCm9LUWRVcDRmbzdqeGJGY0RSazJLTGRZNmtEOU5QaHh1STBTRk9DZjQyeFEvalh6NlVEQ3Q1cGtNdmpUdzBoVVQKTmJSbWtLVFQxSS9oOExxNTUrL1R5eDdiN3ppRzJwRzVRNFQ5VjNndHRJb2NvRFZGbTV6TDFUWFBXSFZ5QW5ucQpPTE9BV3hrL2pmTU1NN01zTnRqZ2Uxc1o3K3E3WXQxYTU4ZGhGbzVPalRmRHFVaERSSlFEZ2ZiVkVyQmRnWVZhCmg4SlNERGVwbHQ4dnZ6M2VQRU0xMEVnU1huaUJReS8zS2tEQjRoblNCSENGQk5CUFRXems0cEZkUDVMZUZ5cTcKZW9uMzdHdHYvM2FqU1Uwby9mYWxsRnQvOVliQ1RHaVAwRmZhNzFHY3VBPT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUgUkVRVUVTVC0tLS0tCg==
signerName: kubernetes.io/kube-apiserver-client
usages:
- client authroot@master:~/Getting-Start-Kubernetes/13# kubectl apply -f csr-app-manager.yaml
certificatesigningrequest.certificates.k8s.io/app-manager created
root@master:~/Getting-Start-Kubernetes/13# kubectl get csr
NAME AGE SIGNERNAME REQUESTOR REQUESTEDDURATION CONDITION
app-manager 24s kubernetes.io/kube-apiserver-client kubernetes-admin <none> Pending
root@master:~/Getting-Start-Kubernetes/13# kubectl certificate approve app-manager
certificatesigningrequest.certificates.k8s.io/app-manager approvedroot@master:~/Getting-Start-Kubernetes/13# kubectl get csr app-manager -o jsonpath='{ .status.certificate}'| base64 -d > app-manager.crt
# context 생성
root@master:~/Getting-Start-Kubernetes/13# kubectl config set-credentials app-manager --client-key=app-manager.key --client-certificate=app-manager.crt --embed-certs=true
User "app-manager" set.root@master:~/Getting-Start-Kubernetes/13# kubectl config set-context app-manager --cluster=kubernetes --user=app-manager
Context "app-manager" created.
# ClusterRole 및 ClusterRoleBinding 생성
root@master:~/Getting-Start-Kubernetes/13# kubectl create clusterrole app-access --verb=create --verb=get --verb=list --verb=update --verb=delete --resource=pods --resource=deployment --resource=service
clusterrole.rbac.authorization.k8s.io/app-access createdroot@master:~/Getting-Start-Kubernetes/13# kubectl create clusterrolebinding app-binding-manager --clusterrole=app-access --user=app-manager
clusterrolebinding.rbac.authorization.k8s.io/app-binding-manager created
# 확인
root@master:~/Getting-Start-Kubernetes/13# kubectl config use-context app-manager
Switched to context "app-manager".root@master:~/Getting-Start-Kubernetes/13# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 20d
mainui-svc ClusterIP 10.97.156.116 <none> 80/TCP 19d
root@master:~/Getting-Start-Kubernetes/13# kubectl get pods
No resources found in default namespace.[참고 영상]
https://www.youtube.com/watch?v=zv24Db73SrU&list=PLApuRlvrZKohLYdvfX-UEFYTE7kfnnY36&index=4